The attention paid to cyber security in the world is on an unprecedented level. This is due to the speed, sophistication and expense of cyberattacks.
In IBM’s Cost of an Data Breach Report 2021, the data breach cost increased between 3.86 million to 3.86 Million to US 4.24 million this is the highest average cost of the 17-year history of the report.
The increase in security was mainly due to the pandemic, which forced workers to work from home. However, the report noted fewer data breaches when an organization adopted the Zero Trust architecture. This is a strong indication of the importance of having an Zero Trust Architecture.
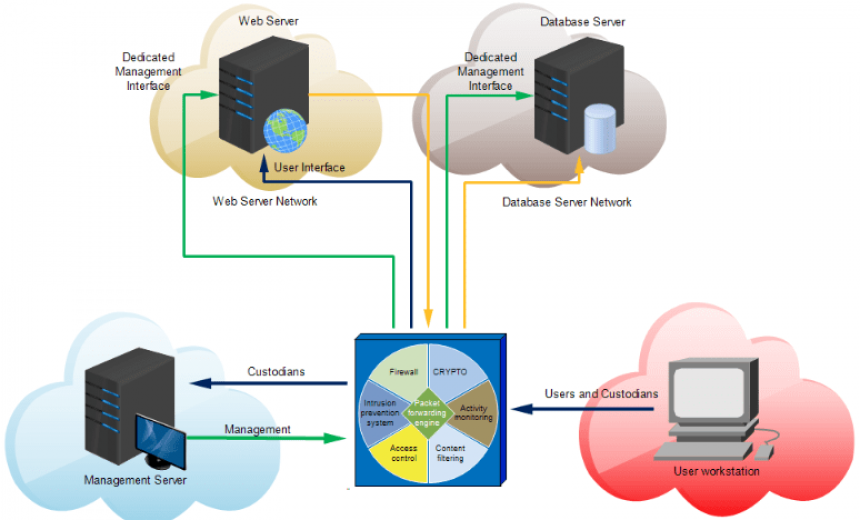
What is a Zero Trust Architecture?
It is important to understand that the Zero Trust model is simple to comprehend. It’s not a singular technology or solution, it is simply a framework on which you can create an entire security system. jackpot city
Zero trust is a firm belief that everything must be hostile. It doesn’t trust any equipment or person, not even employees within the company. Instead, it seeks to ensure that the harm is minimized or reduce to a minimum even in the most dire event that could occur.
As the protection provide is environment-agnostic, applications and services are secured even with cross-organizational communications.
The benefits of Implementing Zero Trust Architecture
Secures Cloud adoption cloud adoption is swift companies often worry about that they will not have access and visibility control. Contrary to that belief, Zero Trust technology and its ability to bring context as well as collaboration and visibility.
Zero trust technologies allow to classify all the assets stored on the cloud, to provide the proper security measures and access control.
Secures privacy of data – Today companies operate within a complex and diverse environment, which makes it challenging to ensure that customers’ personal information secure. Solid authentication and validation that are part of Zero Trust make it possible to protect security of personal data and to build confidence.
Allows for hybrid workforce security: The rapid growth of cloud computing and digitization adoption have led to the concept of remote working. Furthermore, the current outbreak of the flu has made it easier for users to collaborate from any location on any device. This kind of workforce is dispers and needs the correlation of real-time security contexts throughout all domains of security.
Reduces the need for endpoint security: Endpoints in the corporate environment such as servers desktops, laptops, laptops as well as the critical point of Sales (POS) are frequently targeted by hackers in order to gain access to valuable network assets. Furthermore, these endpoints are the most popular way for malware and ransomware to access a network.
While organizations have installed a number of endpoint security tools but these attacks continue. By implementing this Zero Trust architecture, you can place security on your identity as the primary focus of your security and decrease your dependence on traditional solutions to protect your devices.
Supports compliance with regulatory requirements: New regulations such as those of the General Data Protection Regulation (GDPR) as well as the California Consumer Privacy Act (CCPA), HIPAA, and a myriad of other regulations for regulatory compliance are the top priority for companies.
The issue presented by these regulations is securing the data and protecting it. In the Zero Trust architecture, each every time a move is made the payload and identity is verified, which allows to prevent attacks before data is expos. سباق الخيل السعودي
Limits the potential for data exfiltration data: Exfiltration describes as a strategy employed by malicious actors to seek out the transfer, copying, or transfer of sensitive data. It carries out either manually or remotely and is very difficult to identify as it is often similar to access to networks that are justified by the business. In the Zero Trust environment, where everything is monitore, the data is diminishe.
Conclusion
Zero Trust is the latest way to build your security. It offers a set of concepts, ideas and relationships between components that are created to eliminate uncertainties in implementing precise access decisions for the information system and other services. As can be seen from the above, the advantages that come from Zero Trust outweigh its implementation costs , as well as other elements.